Describe and manage Nutanix’s custom Security Technical Implementation Guides (STIGs)
Nutanix STIGs are based on common National Institute of Standards and Technology (NIST) standards that can be applied to multiple baseline requirements, e.g., for the DoD and PCI-DSS.
Nutanix DISA STIG Compliance for RHEL 7 and Nutanix AHV document provides a complete set of RHEL 7 STIG rules configured on NTNX CVM as published by DISA. Nutanix maintains additional (proprietary) STIGs for Acropolis Hypervisor. More information on that can be viewed here.
Nutanix publishes and tests their owns STIGs, incorporating DoD (Department of Defense) STIG guidelines. STIGs are the configuration standards for DOD IA and IA-enabled devices/systems.
Nutanix publishes custom security baseline documents, based on Security Technical Implementation Guides (STIGs) that cover the entire infrastructure stack and prescribe steps to secure deployment in the field.
Not only are these used by the US Federal Government and Department of Defense however, they are also the security configuration standard for many industries that are concerned about security. They can be incredibly comprehensive and run to many hundreds of pages of configuration details. Often each item in a STIG needs to be evaluated independently and the combinations of security settings needs to be tested to ensure they apply the correct hardening, but also do not break the required functionality.
STIG Description
Powerful automation and self-healing security models help maintain continuous security in enterprise cloud environments with efficiency and ease.
Nutanix has created custom STIGs that are based on the guidelines outlined by DISA to keep the enterprise cloud platform within compliance and reduce attack surfaces.
SaltStack & SCMA
Security configuration management automation (SCMA) checks over 800 security entities in the Nutanix Security Technical Implementation Guide (STIGs) that cover both storage and built-in virtualization.
Nutanix leverages SaltStack and SCMA to self-heal any deviation from the security baseline configuration of the operating system and hypervisor to remain in compliance. If any component is found as non-compliant then the component is set back to the supported security settings without any intervention.
- SCMA monitors the deployment periodically for any unknown or unauthorized changes to configurations, and can self-heal from any deviation to remain in compliance.
- For example, automatically protecting permissions on log files is just one of several vulnerabilities that Nutanix checks to ensure their safety.
SaltStack Enterprise, built on Salt open source platform, provides system management software for the software-defined data center with the delivery of event-driven automation for natively integrated configuration management, infrastructure security and compliance, and any cloud or container control.
STIG: Architecture and Design
- Unclassified STIGs are available here: https://iase.disa.mil/stigs/
- Nutanix developed our own Security Technical Implementation Guide (STIG) to speed up the accreditation process for the Department of Defense Information Assurance Certification and Accreditation Process (DIACAP) and the Department of Defense Information Assurance Risk Management Framework (DIARMF).
- Security Technical Implementation Guideline or
STIGs specifies how a computing device must be configured to maximize security.
- The AHV imaged cluster is built to a production standard and it is hardened to meet the STIGs.
SCMA/SaltStack refresh
- Cluster lockdown (system hardening)
- Checks based on DOD STIGs configuration standards
- 800 checks CVM and AHV combined
- sudo salt-call state.highstate (CVM and HV)
- Self-heal from any deviation to remain in compliance
- Run scheduled or manual kick-off
STIG Examples
Configured Name Servers (DISA)
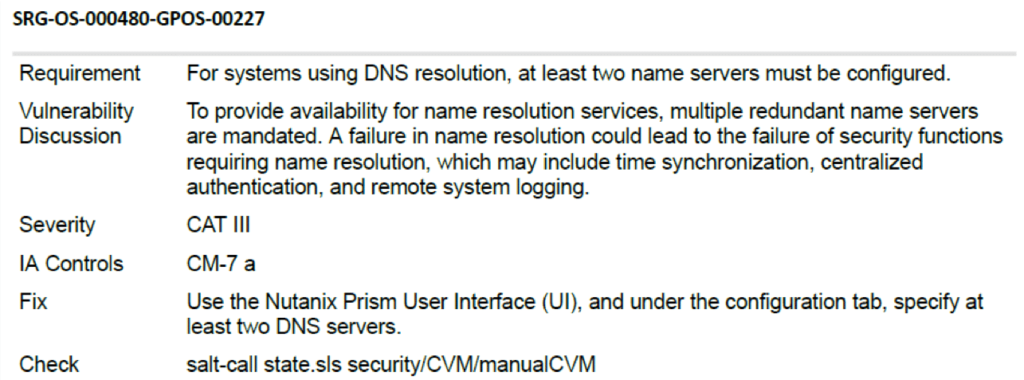
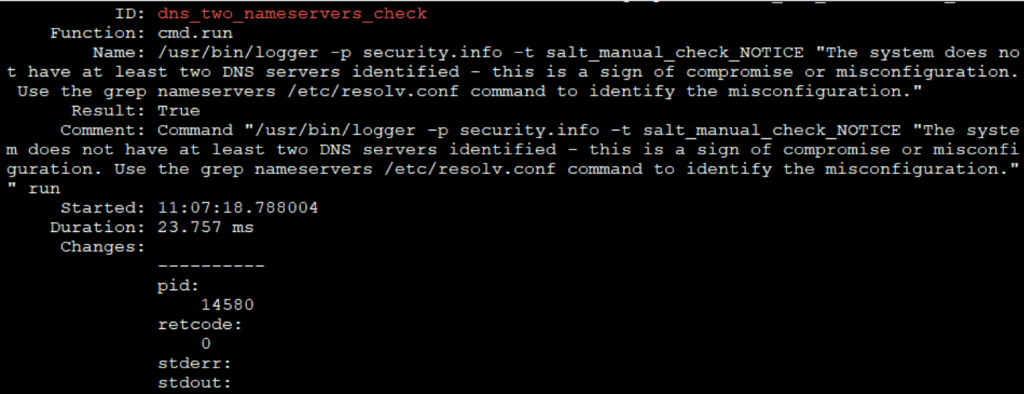
Only a single DNS has been configured, whereas the system expects a minimum of two DNS servers. The STIG file as created in the Home directory (/nutanix/home) by using the below command.
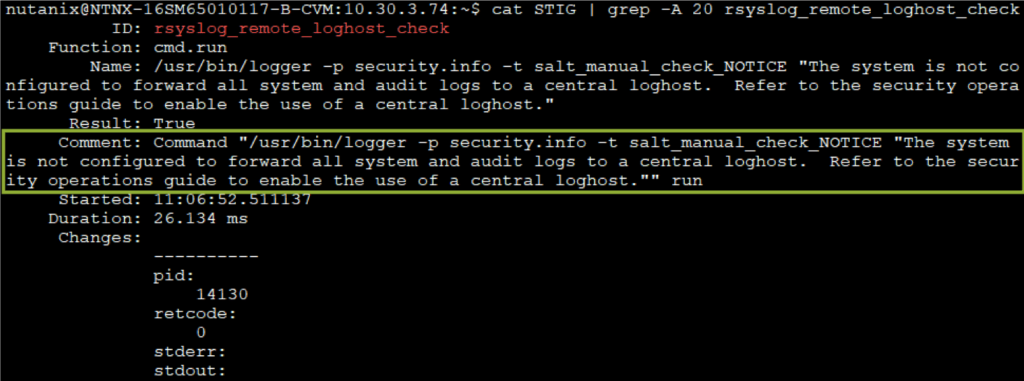
Syslog Server
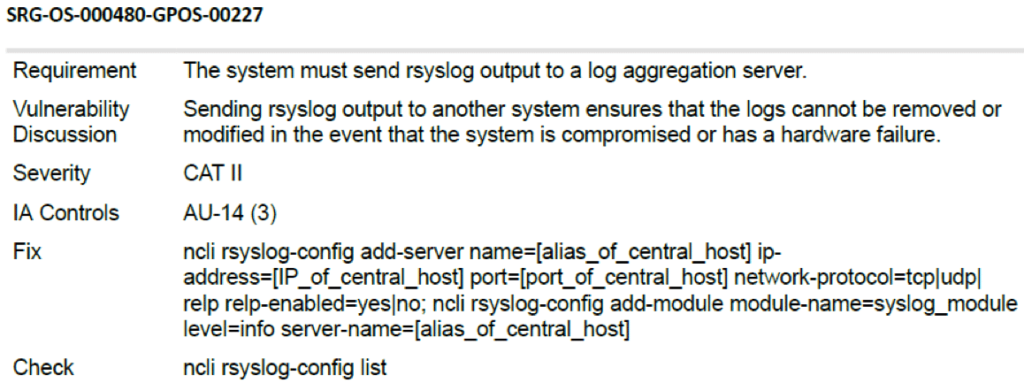
Check ID to search/grep for is: rsyslog_remote_loghost_check. Example: sudo grep –A20 rsyslog_remote_loghost_check. To create what is on the above picture, execute: sudo salt-call –out-file=/tmp/STIG state.highstate.